
All You Need to Know About Data Encryption
In the era of cybercrime and the growing number of data breaches, the issue of information security has become more important than before. Data encryption is important in securing sensitive information through conversion into a unreadable format.
As a business that provides services to people with their customer data or as an individual who strives to be safe online, the encryption is the primary tool of defence. It encrypts data being sent and stored so that it cannot be accessed without authorization.
Furthermore, it is not only the issue of security but even the matter of law that involves encryption. Such laws as GDPR, CCPA, and Indian DPDP Act have strict requirements on using encryption because they want to make sure it would not lead to penalties.
At Redacto, we are dedicated to making business compliance and encryption easier through software such as Data Discovery and Vendor Risk Management that can automate encryption processes.
What is Data Encryption?
Data encryption involves transformation of the readable text (plaintext) to a scrambled form known as ciphertext with the help of algorithms. This will make it so that only authorized users with the proper decryption key will be able to access data.
The main two purposes of encryption are the following:
- Confidentiality: Preventing unauthorized access to sensitive information.
- Integrity: Ensuring that data isn’t tampered with during transmission or storage.
The encryption is done to data-at-rest (stored data) and data in transit (being transferred through online). As an illustration, encryption safeguards cloud-based file storage, emails and online bank transactions.
It is important to note that compliance necessities, such as GDPR and DPDP, require encryption. In its absence, companies will face fines and reputation losses, and even operational delays.
How Encryption Works
Encryption involves a systematic approach to transforming and securing data:
- Encryption Algorithms: Advanced mathematical techniques like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are used to encrypt plaintext into ciphertext.
- Encryption Keys: These are unique sequences required to encrypt and decrypt data. They can either be symmetric (single key for both processes) or asymmetric (separate public and private keys).
Data Categories:
- Data-in-Transit: Encryption protects data being transferred, such as emails and online transactions.
- Data-at-Rest: Encryption safeguards stored files and databases, making them secure against breaches.
Process Overview:
- Input Data → Encryption Algorithm → Ciphertext (Secure) → Transmission → Decryption → Original Plaintext (Authorized Users).
This ensures that even if data is intercepted during transfer or accessed from storage, attackers cannot use it without the decryption key.
Types of Encryption
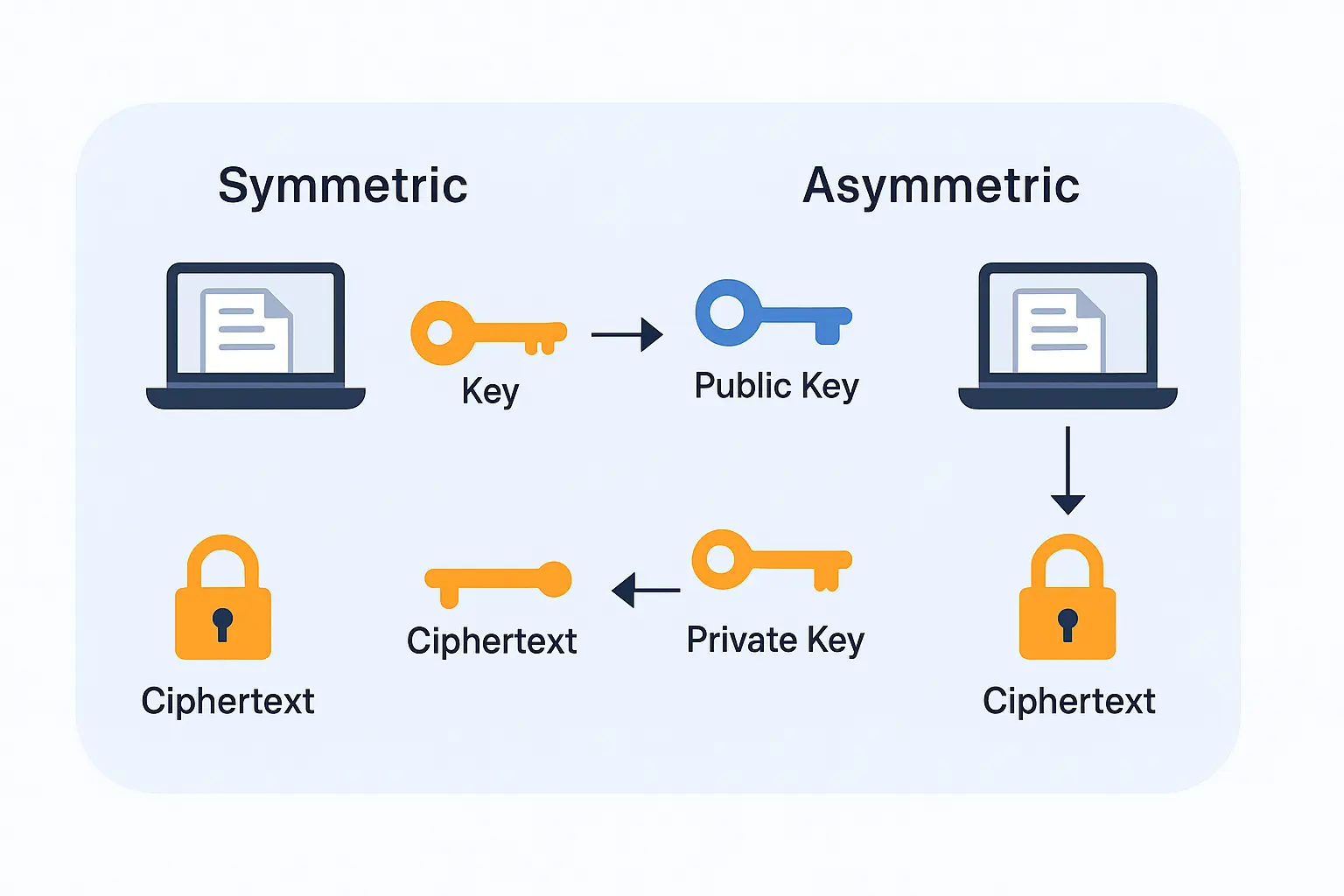
Encryption can be broadly categorized into two types based on how encryption and decryption keys are used. Each has its strengths for specific scenarios.
Symmetric Encryption
Both encryption and decryption processes are accomplished with the same key in symmetric encryption. This is more efficient and quicker in encrypting big data like files and databases.
Well-known algorithms such as AES (Advanced Encryption Standard) are best suited to file storage, secure communication, and backups where speed is important. Protecting the key itself is however a challenge.
Asymmetric Encryption
Asymmetric encryption uses two keys one is a public key to encode information and the other is a secret key to decode information. As compared to the other method, this one is slower but offers improved security hence can be used in making secure communication.
It is commonly applied in email encryption, digital signatures where authentication and data cryptographic integrity are critical. RSA (Rivest-Shamir-Adleman), is one of the popular algorithms.
Applications of Encryption
Encryption aids important security procedures such as securing VPN, transferring files, securing email and securing sensitive information so that it cannot be accessed by unauthorized users. It is essential in the industries as it promotes compliance and trust.
Why Data Encryption is Critical
Encryption is critical for protecting sensitive information and ensuring compliance with data privacy laws. Here are five reasons why it matters:
- Compliance with Regulations: Laws like GDPR, CCPA, and DPDP Act require encryption to protect personal data and avoid penalties.
- Prevention of Data Breaches: Encrypted data remains meaningless to hackers, minimizing exposure in case of breaches.
- Customer Trust: Encryption reassures users that their sensitive data is secure and handled responsibly.
- Protection of Intellectual Property: It safeguards proprietary information, ensuring that trade secrets remain secure.
- Secure Data Sharing: Whether transferring data internally or with third parties, encryption ensures privacy and integrity.
Challenges and Limits of Encryption
Despite its importance, encryption is not without challenges. Here are six common issues:
- Key Management: Losing or mishandling encryption keys can render your data inaccessible even to authorized users.
- Performance Overheads: Advanced encryption techniques can slow down data processing and increase resource demand.
- Human Error: Improper practices, such as sharing passwords or unsecured storage of keys, compromise encryption.
- Outdated Algorithms: Weak or outdated algorithms like MD5 can be vulnerable to modern attacks.
- Insider Threats: Authorized staff may misuse encryption keys, highlighting the importance of access controls.
- Cost and Complexity: Implementing enterprise-grade encryption tools can be costly and operationally challenging for businesses.
While encryption is essential, these challenges can be mitigated with tools like Redacto.io’s Data Discovery, which automates encryption and ensures compliance with security standards.
Conclusion
Encryption of data is the key to digital security. Not only does it secure sensitive information against compromised access, but it also complies with legislations such as GDPR and DPDP.
Redacto is a company that makes it easier to encrypt your information with features such as Vendor Risk Management and Data Discovery, which are designed to accommodate businesses to improve security, and easily attain compliance. Protect your information with automated and scalable solution now!
FAQs
1. What does encryption mean?
Encryption means converting readable information (plaintext) into a secure, unreadable format (ciphertext) to protect sensitive information from unauthorized access.
2. How does encryption help with compliance?
Encryption ensures personal data protection, a requirement under regulations like GDPR, CCPA, and DPDP, helping businesses avoid hefty fines and build user trust.
3. What are the two main types of encryption?
The two types are symmetric encryption (single key for encryption and decryption) and asymmetric encryption (public-private key pair).
4. Why is encryption important for data sharing?
Encryption ensures that sensitive information remains private and secure during transfers, especially in cloud storage or collaboration tools.
5. How can enterprise businesses simplify encryption?
Using tools like Redacto.io’s Data Discovery, businesses can automate encryption, classify sensitive data, and meet global compliance standards effortlessly.




%20Redacto%20logo_New.png)
.jpg)


.jpg)



