
Cyber Security Compliance 101: Regulations, Types & Steps to Start
What if your customers’ private data fell into the wrong hands? With cyberattacks becoming more frequent and sophisticated, companies can no longer afford to take a relaxed approach to data protection. Every company that collects data has a responsibility to protect it, and failing to do so can lead to massive fines, legal headaches, and loss of trust.
Laws such as GDPR, CCPA, and HIPAA are establishing the norm in regard to the way businesses that handle sensitive information have to protect it, and non-compliance is no longer an option. It serves as trust in the current digital economy.
This is where the Trust Centre comes in. With its AI-powered compliance software, Redacto’s Trust Centre assists companies in automating cybersecurity practices and third-party risk management without any hassle, because compliance should not be a burden.
What is Cybersecurity Compliance?
In simple words, cyber security compliance is the adherence to laws, industry standards, and regulations to make sure that sensitive information is processed in a secure manner. It concerns securing data against illegal exploitation, giving businesses a chance to abide by international and local regulations, and avoiding legal consequences.
The backbone of compliance in cyber security lies in the CIA( Confidentiality,Integrity, Availability) Triad:
- Confidentiality, ensuring only authorized individuals can access data.
- Integrity, maintaining the accuracy and trustworthiness of that information.
- Availability, making sure data is accessible when needed.
Be it data security and compliance to protect the financial data or patient information and data under HIPAA or any other law, adherence to cyber security regulations has become integral in today’s world. It’s more than a mandate—it’s a responsibility.
Types of Data Subject to Cybersecurity Compliance

There are several kinds of sensitive information that businesses collect and retain, and they need different protections. Let us take a closer look at the major categories of data and information security compliance regulations:
1. Personal Identifiable Information (PII)
PII contains information such as name and address, phone numbers, email IDs, and social security numbers. Practices like the GDPR require this information to be securely acquired, stored, and processed to safeguard the privacy of individuals and avoid misuse.
2. Financial Data
These involve payment card details, account numbers, and transaction histories that are very sensitive. Security protocols such as PCI DSS guarantee safe processing of financial information, which minimizes fraud-related issues and strengthens the confidence of the customers.
3. Healthcare Information
Patient records, medical histories, and test results are examples of Protected Health Information (PHI) subject to regulations like HIPAA, which precisely prescribes the actions necessary to ensure secrecy and deny unauthorized access to personal health information in the healthcare sphere.
4. Intellectual Property (IP)
Confidential designs and product blueprints, patents, and trade secrets are essential to companies. Verifying them with high-quality cyber security compliance services secures a competitive edge, guarding against data infringement or industrial spying.
Steps to Implement Cybersecurity Compliance
Achieving cyber security compliance may seem complex, but breaking it into actionable steps can simplify the process. Here are essential steps to stay compliant and secure:
1. Understand Applicable Regulations: Identify laws like GDPR or HIPAA relevant to your industry. Understanding their requirements is the foundation of IT security compliance.
2. Conduct Regular Risk Assessments: Evaluate vulnerabilities in your systems, including third-party risks, to identify compliance gaps and risks to data security and compliance.
3. Implement Security Controls: Apply measures like firewalls, encryption, and access controls to protect sensitive information and meet IT security compliance standards.
4. Train Employees: Educate staff about security policies and their role in maintaining cyber security compliance to minimize human errors.
5. Use Automated Compliance Tools: Leverage platforms like Redacto to streamline compliance processes, manage third-party risks, and adhere to regulations like GDPR effortlessly.
Cybersecurity Compliance Regulations

The regulations are crucial to manage personal information security, uphold industry levels, and deter cyber attacks. These are some of the most critical cybersecurity compliance laws that businesses have to comply with:
1. General Data Protection Regulation (GDPR)
GDPR regulates the data protection of every company that operates in the EU or processes the data of EU residents. It requires security processes such as data encryption, breach notifications, and secure processing as required measures against personal identifiable information (PII). Failure to comply attracts huge fines and legal actions.
Another important aspect of GDPR is the necessity of consent and accountability that will demand businesses to demonstrate the data collection, storage, and usage methods. It serves as a pillar to inform data security and compliance in contemporary organizations around the world.
2. California Consumer Privacy Act (CCPA)
CCPA is concerned with safeguarding the personal information of California residents, offering them increased control over the information. It enables its customers to decline the sharing of their data and to remove it.
Compliance involves putting in place systems to deal with consumer rights and systems that cannot be hacked in. This legislation plays a very important role regarding cybersecurity compliance services in the US.
3. Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is a regulation imposed on organizations processing sensitive health-related information, i.e., medical records of patients. It has the strict requirements of data confidentiality, data integrity, and access control to authorized use.
Its adherence guarantees a strong security to Protected Health Information (PHI), which makes it a necessity among healthcare providers and companies utilizing PHI within their operations.
4. Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is aimed at securing credit card transactions and eliminating payment fraud. Any business that processes or stores credit card information is required to meet this standard.
It has stern monitoring measures such as encryption, vulnerability scanning, and a monitoring system, thereby making it the most important need regarding cyber security requirements in financial transactions.
Automate compliance with real-time reports with Redacto
Keeping up with compliance may not be easy, and with constantly changing regulations. Redacto simplifies this by automating the verification of compliance and providing live reports. This will enable the organizations to have control of their data security with ease.
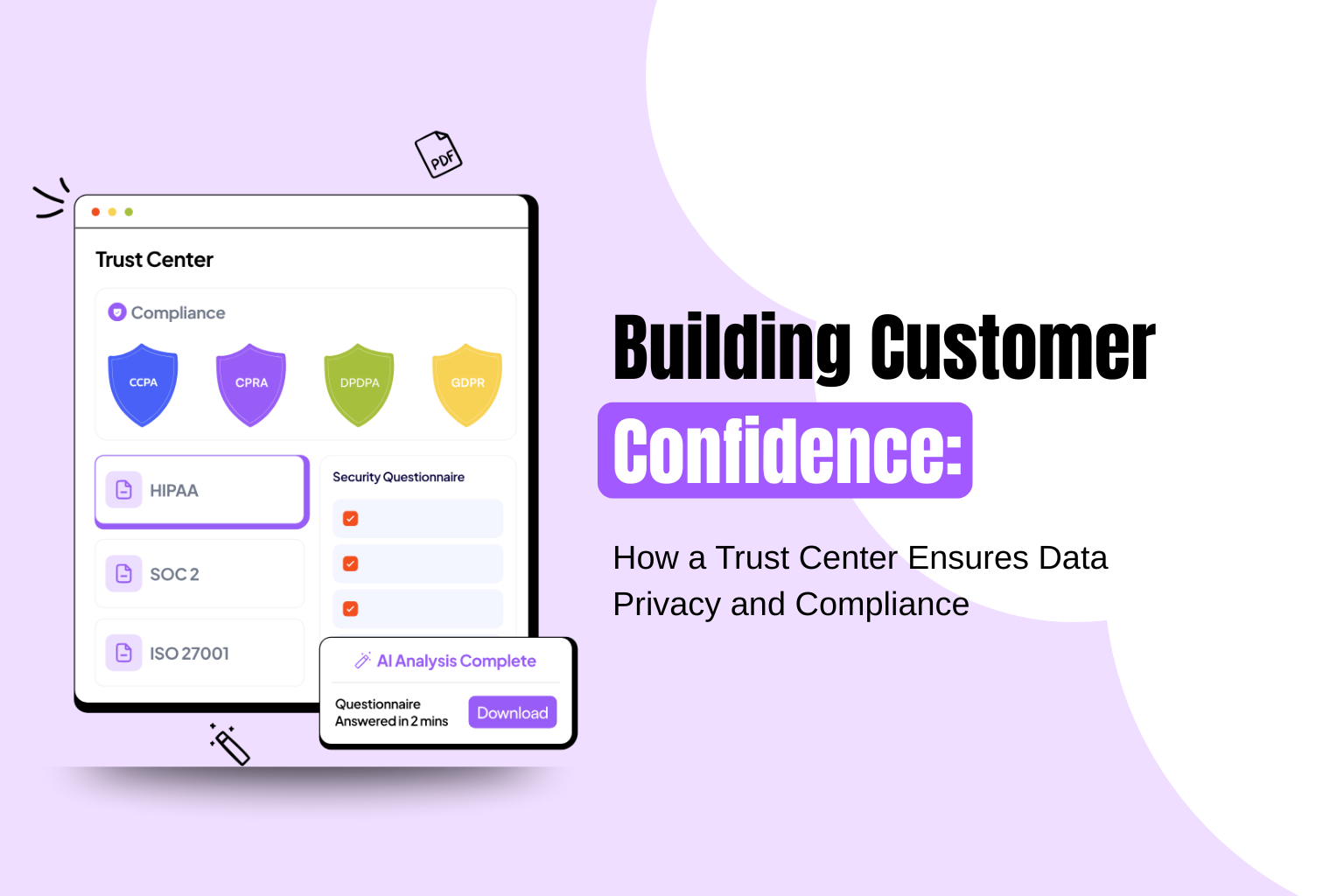
Trust Centre from Redacto offers insights into compliance using laws like GDPR, HIPAA, and CCPA tools. The ability to draw conclusions quickly enables companies to address security gaps and remain ahead.
Trust Centre enables organizations to satisfy compliance and reduce third-party risk with automated work and higher precision with reduced manual effort.
Conclusion
One of the first steps in contemporary business success is cybersecurity compliance. It stores confidential information, maintains compliance with cyber security regulations such as GDPR and CCPA, and reduces the risks of third parties. Solutions like Redacto simplify compliance, building trust effortlessly.
FAQs
1. What is cybersecurity compliance?
Cybersecurity compliance ensures businesses follow rules and laws to protect sensitive data like PII, financial records, and intellectual property from breaches or misuse.
2. Why is cybersecurity compliance important?
It helps prevent data breaches, builds customer trust, and avoids penalties for non-compliance with laws like GDPR and HIPAA. Compliance strengthens overall IT security systems.
3. What are some key cybersecurity regulations?
Prominent cyber security regulations include GDPR, CCPA, HIPAA, PCI DSS, ISO 27001, and NIST frameworks, each focusing on safeguarding sensitive information based on industry needs.
4. How does Redacto automate compliance?
Redacto uses AI-powered tools to generate real-time reports, monitor risks, and ensure adherence to regulations, reducing manual effort and errors while managing third-party risks effectively.
5. What industries need cybersecurity compliance?
Industries like finance, healthcare, insurance, and e-commerce must prioritize compliance to safeguard sensitive data and adhere to relevant cyber security regulations like GDPR or HIPAA.




%20Redacto%20logo_New.png)



.jpg)

.jpg)
